The OSINT Newsletter - Issue #14
Tools, tactics, and techniques for network analysis using OSINT
Open source intelligence can be used for good or bad reasons. Often, the tools and techniques used by ethical practitioners are identical to black hat threat actors. Because of this, many people ask whether a data source or tool is ethical or not. This is particularly true when looking at credential dumps or collecting information from password recovery methods.
My general take is to use all of the tools and information that are available to you within reason and make sure you can justify your means with your ends. A bad actor can analyze a person’s Facebook profile to get their pet’s name or high school mascot, leading to a successful security question answer. That doesn’t mean that analyzing a Facebook profile is black hat.
Just do good. Don’t commit crimes. Don’t be sketchy.
Now, let’s get back to The OSINT Newsletter. This issue is about network analysis.
OSINT Tools
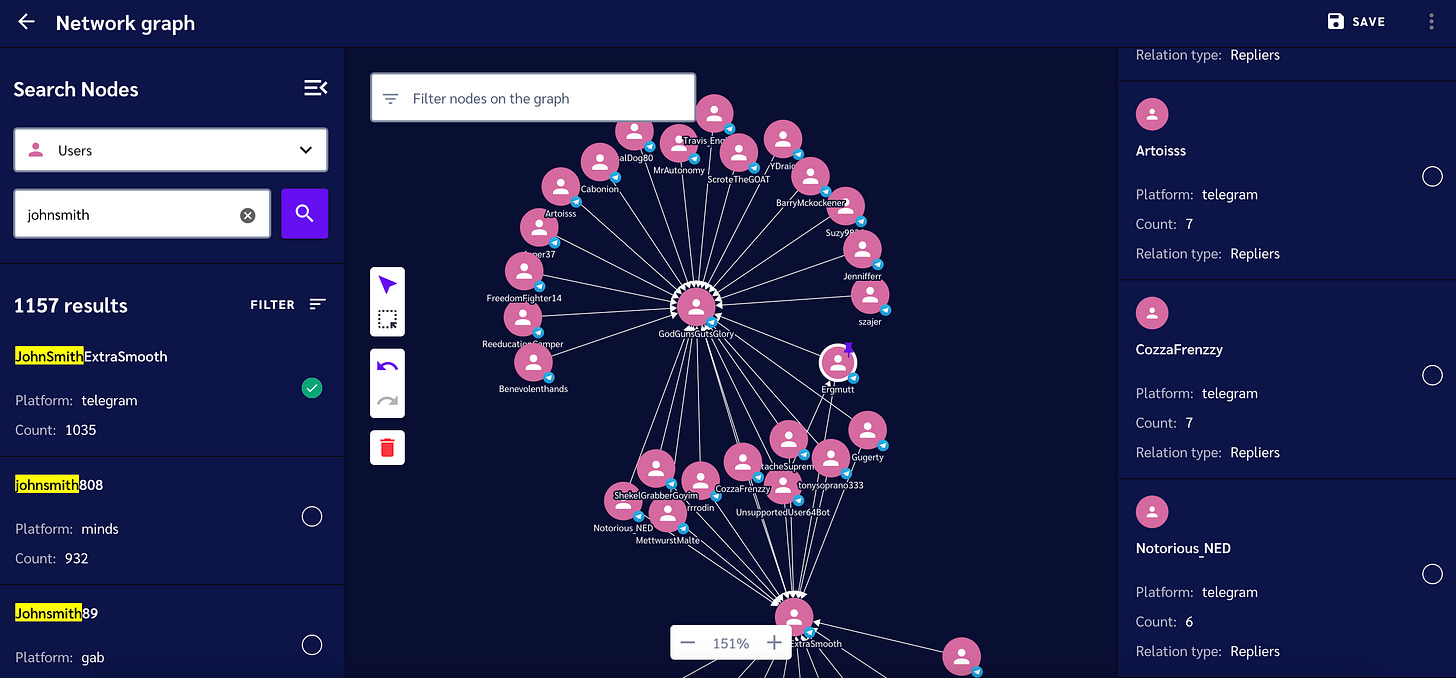
SMAT Network Graph - Limited Release
SMAT is an open source dataset designed to help researchers, activists, journalists, and other organizations track and analyze hate speech and mis/disinformation online. I’ve frequently referenced SMAT over the years through my tools like Ruby, and Banana Hands. Now, the folks at SMAT have built a network graphing tool that allows you to connect the dots. I’ve received early access and I’ll have to say, I’m impressed.
What’s great about the SMAT network graph is that it allows you to search for a single username, hashtag, URL, or channel; then, it has a simple-to-use interface that allows you to expand your network map one node at a time, or in bulk.
You can find all the URLs that a username on Telegram has mentioned, for example, then find other users who also mention that URL.
Another thing I enjoy about this tool is the fuzzy match on usernames, which you can see in the image above. This doesn’t limit you the way other username tools do with exact matching.
This tool is still in beta at the time of this writing. Check out the link in the title to see about getting access.
Quidam - Script | Maltego Transform
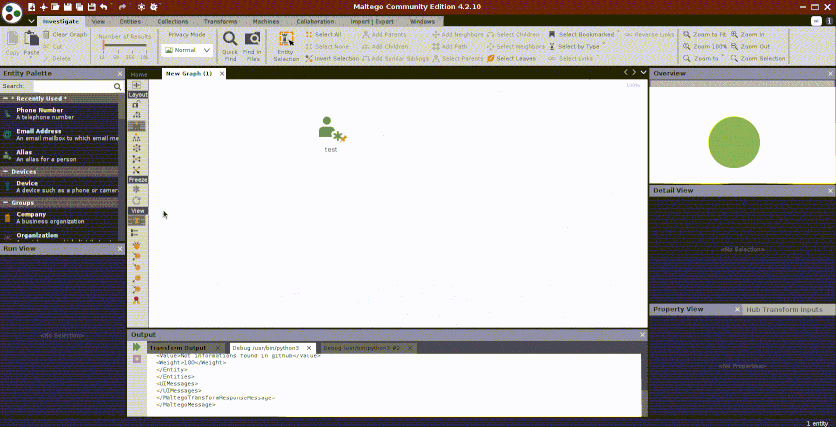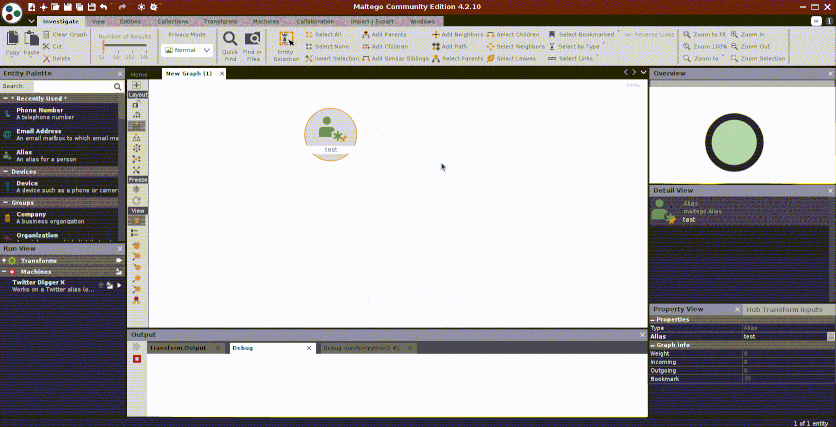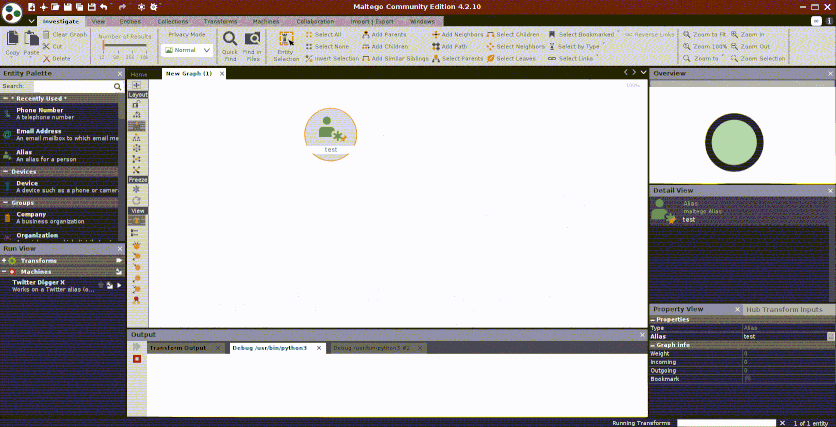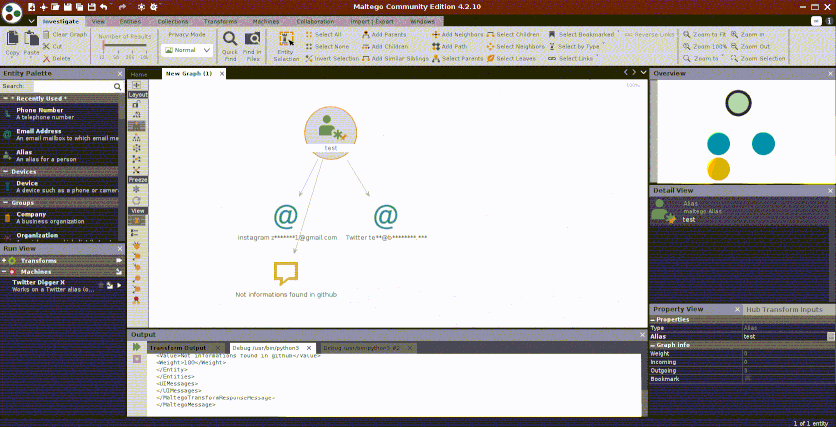
Quidam isn’t necessarily a network analysis tool, but because of its related Maltego transform, it can easily be used in that context. The methods used to extract information in Quidam are in that grey area ethically. It leverages the forgotten password function to determine if a username is associated with an account. This is similar to the tool Holehe, but instead of emails, it’s looking at usernames.
In conjunction with the SMAT network graph, you can begin investigating usernames associated with a particular channel, URL, or hashtag and then leverage Quidam to see if those accounts are associated with Instagram, Twitter, or Github. Because SMAT is mainly focused on fringe social media platforms such as Gab, Parler, 4chan, etc. (not exclusively, but mainly), chaining these two tools together is a great way to expand your research from edge to center online.
Maltego Transform Template - Soxoj’s template
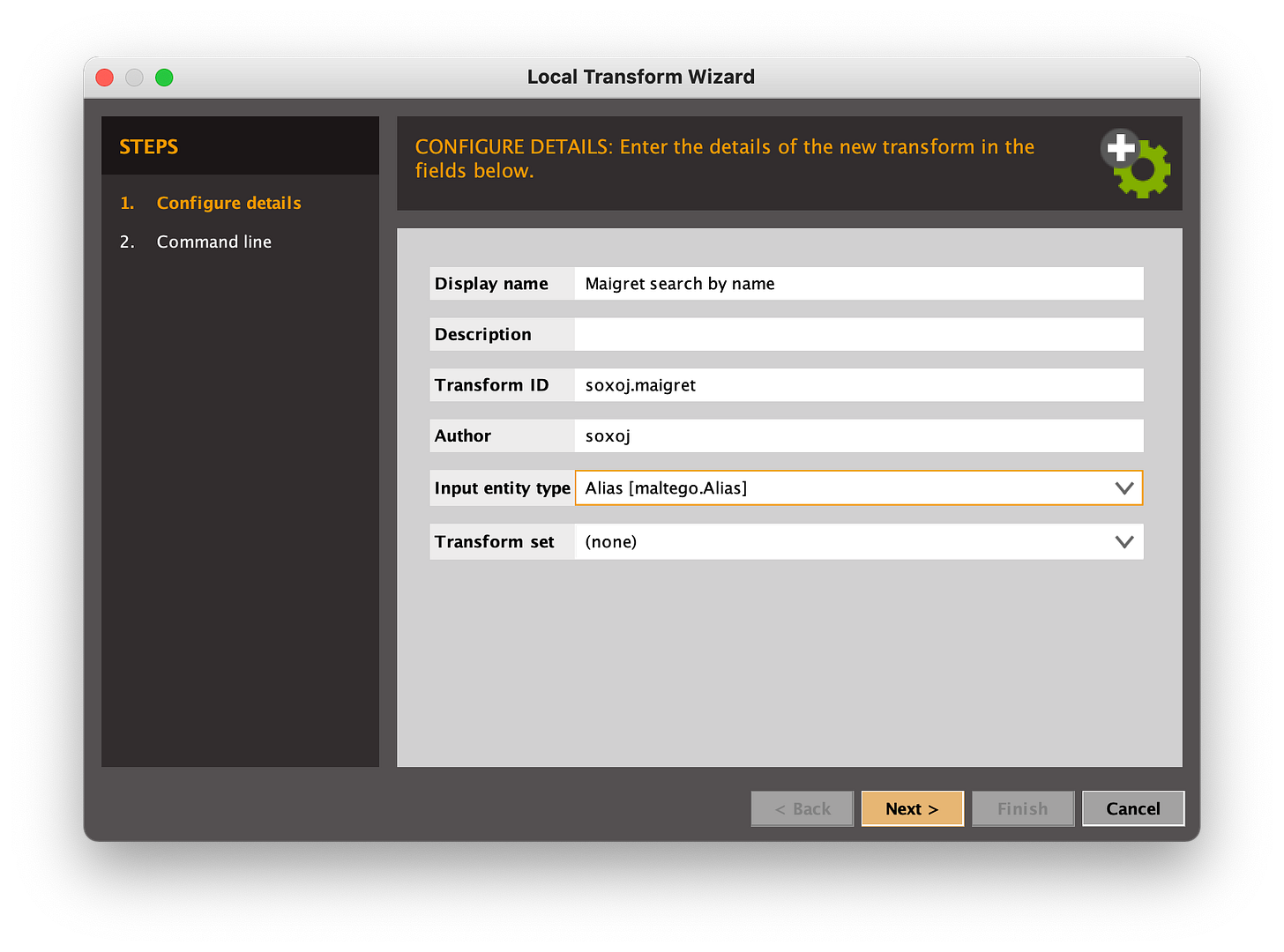
If you’re interested in network analysis with OSINT but can’t find the tool you’re looking for or you use a tool that doesn’t have a graphing function, consider making your own Maltego transform if you can write Python. Soxoj put together a template they used to build the Maigret Maltego transform locally. If you haven’t heard of Maigret, it’s a very capable reverse username checker.
Like SMAT and Quidam, you can use the Maltego transform Soxoj built to continue your OSINT network analysis starting with a username.
What I like about this template is that you don’t have to digest and understand the Maltego API documentation (although I recommend it) if you don’t want to. It also allows you to take scripts that you’ve already written and turn them into Maltego transforms you can run on the community edition.
Remember #OSINT != tools. Tools help you plan and collect data but the end result of that tool is not OSINT. You have to analyze, verify, receive feedback, refine, and produce a final, actionable product of value before it can be called intelligence.
This is the end of the free subscription to The OSINT Newsletter. To see practical applications of OSINT tactics and techniques, please consider supporting this publication with a paid subscription.
Paid subscribers get access to practical OSINT tactics and techniques I haven’t published publicly online. This issue explores practical applications for network analysis in addition to step-by-step guides for OSINT techniques.